Data Security
A fully end to end encrypted network with device based latency protections.
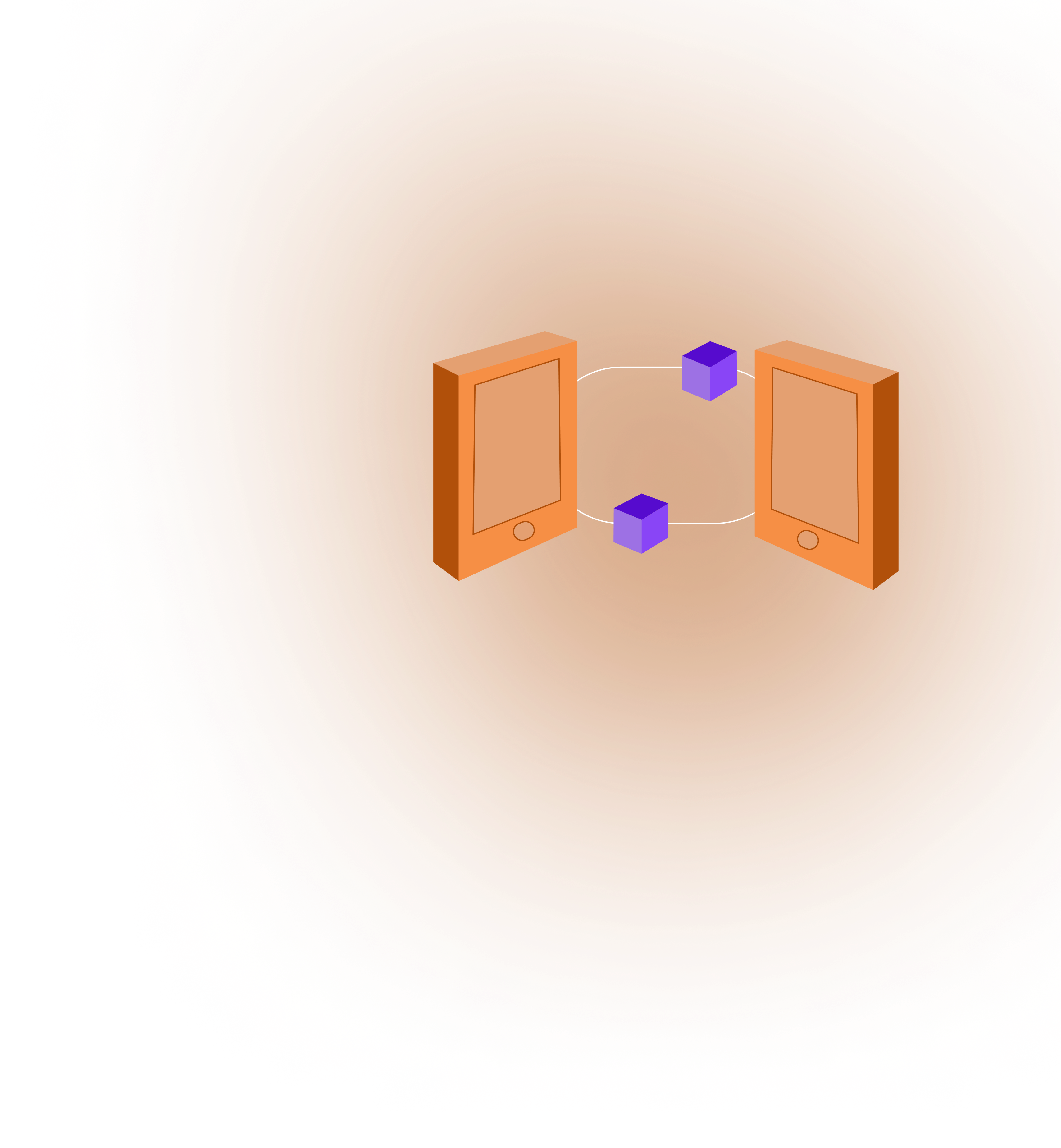
Data is encrypted on-device before network transmission and reconstructed for end users. Multi-ring logins secure hardware and account access. Latency variables help flag unusual behavior while maintaining a robust connection.
8ms
Network Authentication
100,000
Server calls for $1
Default Private File Storage
Enhanced data security to improve compliance and halt data breaches. Granular access controls enable companies to define user permissions and maintain a clear audit trail, ultimately streamlining data management processes and fostering a more efficient and secure working environment.

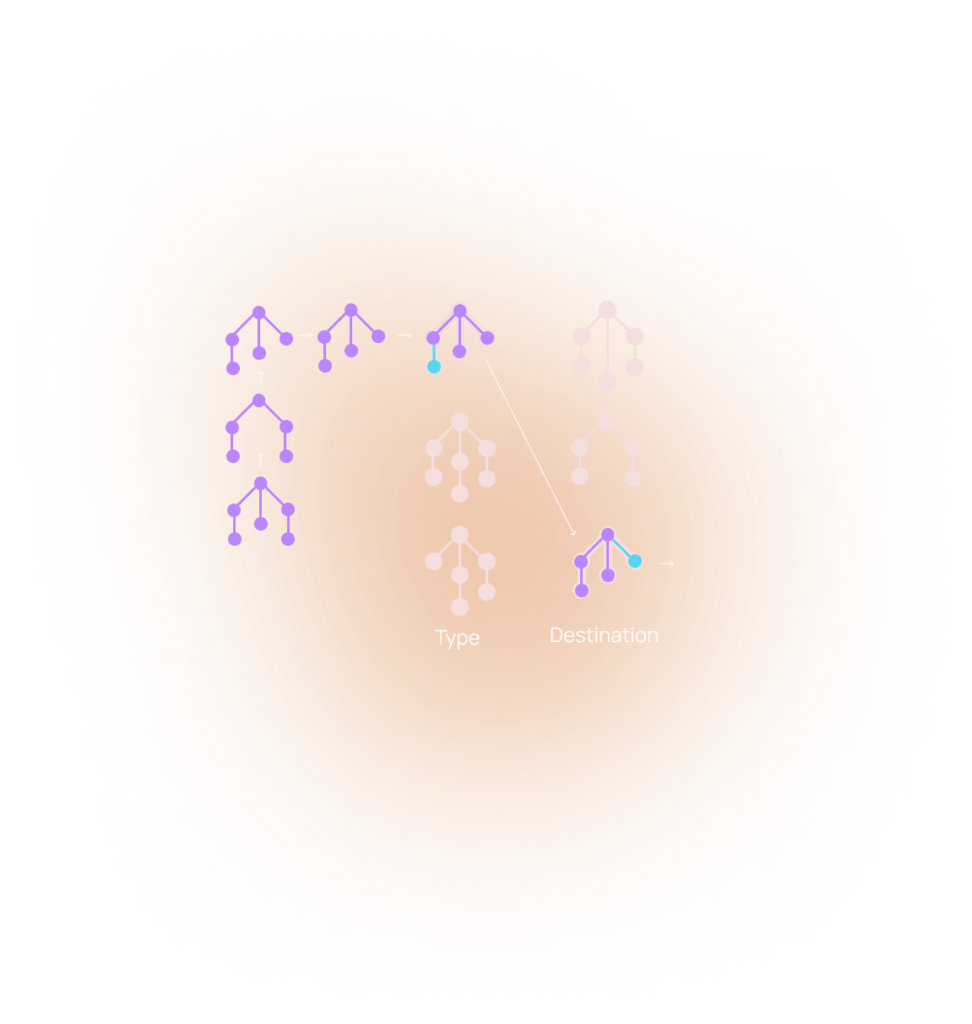
Secure Communication
Every communication is multi-party encrypted with unique key ids for every endpoint. Data remains encrypted until reaching its intended target through Embedded Data Routing; which can discern the destination and data type to ensure compliance without knowing the accompanying message content.
Behavioral Security
Detect activity anomalies the moment they happen with Advanced AI security that measures and authenticates latency variables. If an account messages the network in a way that conflicts with it’s behavioral persona the account requests are denied immediately pending re-authentication.

Try the Network
Experience the fastest communication on the planet with network requests that arrive internationally in milliseconds while hitting 80% fewer computers along the way

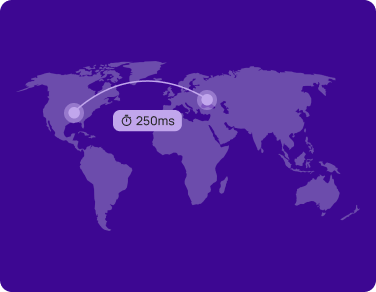
Find a friend on another continent and transfer them permissions with a speed the Google Cloud Team claims “Shouldn’t be possible.

Take embedded compute offline and transfer it via blue-tooth to colleagues without a network connection.

